Rather you purchased a new laptop from Best Buy or was issued one from your IT department the odds are it came with antivirus software. Antivirus software is designed to detect and ultimately quarantine and remove viruses from machines.
Antivirus software mitigates many forms of malware such as keyloggers, backdoor, trojan horses, and so on. Up until a few years ago antivirus software relied on signatures to detect this malicious software and therefore was only as good as the signatures. As APT (Advance Persistent Threats) grew along with zero day vulnerabilities signatures became less reliable.
This in turned caused antivirus companies to become less reliant on signatures and move to anomaly detections. For example Carbon Black uses behavioral detection which was done by building context around every process execution path. In addition to behavioral detections other techniques were deployed such as sand-boxing, data mining, advanced heuristics, and rootkit detections.
Even with all these advancements of antivirus software, endpoints are still consistently being exploited and remain a security challenge. The latest ransomware attacks such as WannaCry that impacted entire industries is case and point.
In a recent article Alex Stamos (former Facebook CSO) was quoted, ““The truth is within the security and safety space, you’re not building a bridge where you’re done. You’re playing chess. But it’s an infinite game of chess where your adversary you’re playing against constantly switches out.”
In looking to secure endpoints this means we cannot rely on a single solution such as antivirus software. Today’s mobile world where employees and users take their devices and connect to unsafe WiFi access points (local coffee shop, hotel, airport — see WiFi security) threats will only advance. Just like in chess you have to play 3 moves ahead at a minimum just to keep to up.
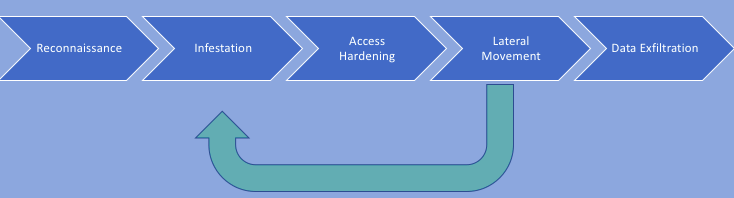
Let’s look at how we can augment antivirus software to help protect endpoints. To do this let’s look at a common kill chain. In order for any exploit to be effective there is either luck or good reconnaissance.
Reconnaissance: Some examples could be better understanding the end user (browsing LinkedIn, Facebook, etc.) to conduct a spear phishing attack (trying to get someone to click a link or open a file). It could also be scanning a system to understand the operating system to know which vulnerabilities could be exploited.
For endpoint security some of the best counter measures for reconnaissance is security awareness training and patching systems. With security awareness you can teach end users about how to avoid social engineering and not connecting to untrusted sources. Patching systems will keep the vulnerabilities to a minimum and hardening systems (enabling firewalls like Symantec) make it harder for scanning of devices.
Infestation: This is where the attack actually takes place. This could be the end user clicking on link, downloading infected files, a worm moving laterally etc. One of the best approaches here is to stop the device before infestation occurs. How?
Malware typically relies on DNS (Domain Name System) to start infestation. Let’s look at a sample use case where a end user clicks on a malicious link or browses to a infested site say (www.goo.com). Using DNS www.goo.com lookup returns an IP address of 185.34.213.21. If malware detections are set at the DNS layer then when the end user clicks on the malicious link DNS could for example send them a blocked page or a 404 not found.
While DNS is a great first line, attackers are creative and use avoidance techniques. Staying on the DNS theme one of the avoidance is registering hundreds of random domains that make it difficult for DNS to know what’s good and bad. So when looking at DNS layered security its best to use one that has great threat intelligence. Akamai’s Enterprise Threat Protector is a great example of this and given that it sees literally trillions of DNS request daily its a great choice for DNS layered protection. Cisco Umbrella and InfoBlox RPZ are other examples rDNS based solutions.
But what about malicious file drops where say an attacker uses Facebook or other known sites to spread malicious files. This is where the second step comes in to play with secure internet gateways / secure web gateways. These solutions allow for the proxying of traffic to detect malware before it reaches its destination. Proxying traffic looks like this client –> proxy server –> destination server. So in the case of a malicious file drop the server connects to the proxy server that detects malicious traffic before its sent back to the client.
Its important to remember how DNS works to ensure that off network devices are still protected. DNS servers are set when a client machines connects to an access points. Access points use DHCP (Dynamic Host Control Protocol) to provide the client with an internal IP address as well as sets the DNS server to use for DNS resolution. When a client connects to their local Starbucks Wi-Fi it will set the DNS server for that device. Its important when considering DNS solutions to choose one that provides a “shim” that can be installed locally on the device so when roaming off network DNS traffic will still use resolvers that are set up to protect against malicious domains.
Infestation at this point will be dramatically reduced by using these techniques to reduce the overall attack surface. It’s been reported that up to 90% reduction of malware by effectively using rDNS and proxy solutions. For the other 10% there is still the antivirus agent there for detection and clean up.
With zero day exploits nothing is 100% and infections will still occur so let’s continue to follow the kill chain and look for techniques for mitigation.
Access Hardening: Once malware reaches it’s destination it wants to make itself hard to detect and remove. In security we talk about polymorphic malware which is a type of malware that constantly changes its identifiable features in order to evade detection. In some instances this makes quarantine and removing the malware almost impossible. In ransomware cases the machine becomes encrypted and unaccessible.
At this point its best to have recovery techniques. Example of this would be backups to restore the machine to a last known good state. Virtualization is also used at this point where virtual machines can easily spin up/down thus removing any malware that might have been installed.
Lateral movement: SANS – Eric Cole, Ph.D wrote: “In recognizing that attackers will succeed, the goal becomes minimizing the exposure and damage. This correlates into two key metrics… dwell time and lateral movement.” To make matters more frustrating in 2016 Fireye reported that the mean dwell time was 146 days. So not only will the attacker be able to spread through lateral movements but the likelihood is that it’ll go unnoticed.”
Larteral movement is malware spreading throughout the environment from machine to machine trying to infect as many compute devices as possible. The best countermeasures are two fold – network segmentation and application based access.
Network segmentation refers to segmenting your network with typically nextgen firewalls. This is where sensor placement is used for intrusion detection and prevention. When malware tries to move laterally this limits the amount of machines that could potentially get infected thus further reducing the attack surface. Checkpoint and Palo Alto are great solutions for micro segmentation.
Application based access means moving away from a traditional network based approach. Traditional network based access provides malware the ability to move across the network by exploiting basic networking principles. For example if device A is on the same network as device B then device A can send packets to device B. Depending on placement of sensors, HIDS, logging, and a multitude of other factors this communication typically goes undetected. Google BeyondCrop and Akamai’s ZeroTrust solutions move the authentication and authorization to Identity Aware Proxies and provides access only to specific applications further reducing the attack surface. It should be worth noting that PAM (privileged access management) should be considered at this point as well.
Data Exfiltration: Data exfiltration is where malware will try to communicate to a command and control server or exfiltrate data. This is where DNS comes back into to play as it can be detected before communication goes outbound. At this point you’ll want a rDNS solution that has sink hole capabilities where the traffic can be directed. By doing this the actual end point can be identified as well as any IOC (Indicators of Compromise).
Appropriate configurations of outbound inspection at firewalls as well as DLP (data loss prevention) should be used at this point. By following best practices for security hygiene will help before loss of a data breach from malware infestation.
In short its not enough to rely on antivirus for end point security protection. Rather a multi faceted approach will help keep you organization better protected.