
Overview: Atlanta was recently a victim of a ransomware attack. Ransomware as the name implies is a type of software that will encrypt all the files on your computer and will not release a key/password until a ransom is paid. Atlanta is not the first nor will they be the last to experience this type of attack.
Early last year a ransomware called “WannaCry” was released and caused major disruptions across the globe. The U.S. wasn’t as impacted as most countries primarily due to geography and stricter adherence to patch updates. Systems that are not updated are exponentially more vulnerable then patched systems.
Fundamental Architecture Problems: Atlanta Mayor Keisha Bottoms said in a press conference that “there will be significant investments to ensure these types of security incidents don’t happen in the future.”
History has shown that these types of investments typically go into proactive controls like automated backups and patch updates, NGFW, HIDS, IPS, etc. While items like automated updates will go a long way to make sure patches are applied this will not keep the bad guys out. Why? The problem is that this traditional build out of moats and walls / defense in-depth is just not working.
Traditional architectures focused on creating a DMZ (demilitarized zone) where you would place servers between multiple layer of firewalls. The diagram below shows what a DMZ set-up might look like:
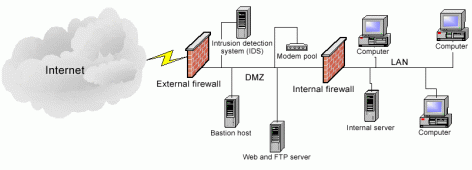
There are two fundamental flaws in this reference architecture. First is that firewalls are designed to keep things out but we just keep opening ports. By doing this it allows for inbound connections before any type of trust is established. Secondly once the firewall is breached the attack can spread through lateral network access. This is one of the reasons why attacks proliferate so quickly.
Inbound Connection Challenge: When organizations first started building out their networks they focused on building out LAN environments and connecting them to MAN/WAN infrastructures. As the internet evolved there was a need to let traffic that was not on the corporate network to come inbound. In order to accommodate this routers were built with firewall controls.
As technology advanced proxy servers become more prevalent. There are several types of proxy servers such of forward proxies and reverse proxy. The primary difference between a proxy server and a traditional firewall is that the proxy servers add another connection. So instead of a direct connection from User to DC it would be a connection from User to Proxy to DC.
When we look at the latest reference architectures from Google BeyondCorp there’s reference to proxy technologies to overcome this inbound connection challenge. By proxying all inbound requests you can also authenticate before allowing access. This is an important distinction from a traditional proxy set-up. By using proxy servers in conjunction with access management capabilities it will not only increase the overall security posture but can create efficiencies by deploying techniques such SSO (Single Sign On).
Fundamental Change: Major trends are driving the need to shift security strategies. As more users / employees move off corporate networks and more applications / infrastructure moves to the cloud so should our security architecture. The biggest fundamental change is that we can no longer trust that local IP’s are safe. Making a shift from network based access to application based access. There’s no longer the idea of internal vs external users as they should be treated as the same.
This also means that we need to ensure that client endpoints are secure and updated (see recent Bluetooth exploit). In hybrid architectures if client / employee end points are not secure then there’s potential security holes. Also for end points two factor authentication should be required for all assets. Relying on passwords has never really worked and that should just be accepted.
Additional Benefits: There are several business benfits to moving to a new reference architecture other than an increase in security posture. This reference model can decrease cost by removing expensive hardware. There are organizational benefits, for example, integrating access management with HR systems.