
Managing identities correctly will not only give your business a competitive advantage but it will also make you more secure.
Rather you are managing employee, customer, or contractor identities you must take into consideration how you are going to not only use this information but also how to keep it secure. If you don’t have the correct policies, procedures, and systems in place you are putting not only the identity of the people at risk but also your business.
Take GDPR, which is the new EU regulation for data privacy, as an example. The penalty under this new regulation can be as high as 4% total revenue. Regulatory fines are not the only risk as you could lose customers, employee data can be used to access sensitive systems, and much more.
Since the begin of the internet there needed to be directory in which information about country, organizational unit, people, etc. could be stored. This led to the X.500 directory standard which provided a means for hierarchical structures to be generated. Over time this evolved into what is in common use today LDAP (Lightweight Directory Access Protocol). All major directory services like Active Directory, eDirectory, and Apache Directory Server support LDAP.
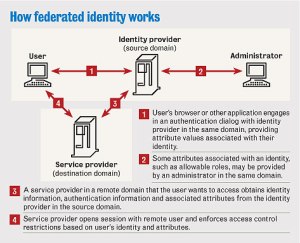 As more and more systems and networks came online there became a need for federated identities. Federation is linking one identity across multiple identity management systems. Solving the federation challenge also provided for a more robust SSO (Single Sign On) experience, most notably SAML.
As more and more systems and networks came online there became a need for federated identities. Federation is linking one identity across multiple identity management systems. Solving the federation challenge also provided for a more robust SSO (Single Sign On) experience, most notably SAML.
As more of our customers came online there was a need to better serve them digitally. Organizations that thrive in a digital world understand the want/needs of the consumer. This competitive advantage is driving the adoption of CIAM (Customer Identitiy and Access Management) solutions.
As social media and e-commerce exploded customers desired the use of a single identity. As Marshall Field was famously quoted as saying “Give the lady what she wants”. In order to provide this OAuth and OpenID were developed. An example of how this can be used is when a user/customer uses their Facebook credentials to login to an e-commerce site. Almost everyone has an account with one FANG (Facebook, Amazon, Netflix, Google).
Rather you are beginning a new project, starting a new business, or trying to revamp your digital experience here are 6 key things to consider when it comes to managing identities.
- What kind of identity do you collect, create, and/or store? By first answering these question it will help in the overall design of the system. For small business that need to digitally authenticate customers it’s wise to chose/build a system that will integrate with OAuth. If you are a bank or other heavily regulated industry you’re probably better off with choosing a different IdP.
- Today most organizations still rely on internal directories to authenticate users. It’s not uncommon to want to move a directory server to the DMZ to authenticate external users. In fact Microsoft has published documentation on how to do this. While this might solve short-term needs this will limit scale and flexibility and quite frankly a risk most senior security professionals won’t accept. It’d be advised to consider an external IdP. There are many to choose from such as Okta, Ping, OneLogin, etc.
- G2Expert recommends coupling IdP which access management technology which supports a zero trust model. CIAM technology from providers such as Janrain provides organizations the capability to gain visibility into their customers to provide a better UX and increase revenue. It also helps to reduce fraud as well as increase compliance with regulations such as GDPR.
- Just like customer identities you should consider employee and contractors identities in conjunction with access management. Akamai’s Enterprise Application Access provides access management supporting zero trust principles with a simple HTML5 browser.
- Privileged Access Management helps organizations restrict privileged access by enforcing least privileged security principles. For example, CyberArk provide a SecureIdP with Privilege Account Security solutions.
- Strong authentication MFA. Almost all solutions on the market provide some MFA capabilities with leading vendors providing advance capabilities. We like Duo Security for its ease of integration and out of the box platforms supported.
It’s important to remember that identity management solutions are not a one-size fits all. Every organization must determine their own needs based on easy of integration, risk appetite, regulatory environment and of course cost.